
In dialogue with Ferdinand Doblhammer
– How did you develop your interest in media art, music, and design?
I‘ve always been fascinated by computers of any kind, visiting computer fairs at a very young age – one of the first words I could pronounce was the name of the fair. I initially studied graphic design, which thought me a lot about symbolism and the correct use of certain aesthetics. While always keeping an eye on new technological advancements, it was only at the end of my design studies that I discovered media art. In parallel I also started writing electronic music and now im happy that I can combine all of that stuff.

– Have you ever used classical artistic mediums like painting or sculpture and if so, why did you abandon them?
I used to draw a lot, but I wouldn’t necessarily say that I was too invested, so it never felt like I was abandoning anything; I like producing things with my (real) hands; it‘s very relaxing – though I feel that the mouse cursor works a bit better for me. I often wonder, when the cursor will absolutely obsolete or maybe even seen as a classical way of forming things.
– Can you describe how you address the issue of data security in your works?
Almost all of my media art works deal with this topic in one way or another. I think we should be very concerned with the way data is accumulating and how freely available these strings of information already are. There should be light shined on how the use of combinations of our data affects our living and shapes our quite fragile futures. There is a need to sharpen the senses for these possibly problematic and dangerous combinations.
By turning machines and their data against themselves, showing their sheer size or generating content out of what is seemingly unimportant I am trying to transmit a feeling of the digital whereabouts we are – sometimes unknowingly – slithering into.

– Can you discuss the borders and border crossings that your works aim to explore?
A lot of borders are just made up things or socially/politically constructed. The border can only be felt when crossing it or walking just by it and I have a particular interest where these borders are and how they manifest; especially in the digital realms there are a lot of invisible lines to explore. Internet content censorship is definitely one of the more hidden ones – as someone who was brought up to find the internet as an infinite open space it is hard for me to grasp some people just cannot see the same things. Personalisation algorithms will make this worse.


Working with drones I realized, that especially war drones kind of skip the borders.
On one hand they fly just over it and can be practically everywhere, on the other hand there is this weird ambivalence of the operator that sees the target on the screen and crosses the border digitally. All of them are practically in the same space, although the operator cannot be seen. This is also one of the topics Patryk Senwicki and I tried to outline with our work ‚Inherent Resolve‘, where a war drone is placed in AR in your space in it’s real size. Another work we did together is „Ephemeral Borders“, an Instagram-AR-Filter where you could place a barbed wire fence in your room.
– How do you use augmented reality, video, and installation to highlight the problems of media policies in today’s world?

What I personally like about AR/XR is the possibility to show 3D objects in their real size, that are either hard to show otherwise because of their sheer size/accessability or because they break physical boundaries. Placed at the right spot, they can work as political interventions, putting a critical layer over original objects that can be explored. Although, I still think there needs to be some kind of a lead-in, as a lot of people are not too familiar with the technique yet. At the moment speaking, it can fill a gap between video and installation, telling short vivid stories, or that’s what I like to used for.
– Can you explain your collaboration with the dancer and choreographer Lea Karnutsch? How do you combine dance with media art in your performances?
Lea and I are trying to show hidden digital processes through the means of performance. These processes are often quite abstract and ungraspable – and even though they are basically everywhere and crucial to our everyday life, we lack emotional bond to them. The physical components of body and hardware together represent situations and characters that are inherited in named processes.
Together we have a collective called Flip The Coin, our pieces always contain contemporary dance, music exclusively written by me and a reactive/interactive stage object that forms a base for the choreography and story. After choosing a topic we want to address, all of the things are developed at the same time, so the choreography and music are not written for the stage piece – they grow in symbiosis.

– Can you share your experience participating in various exhibitions, such as Parallel Vienna 2020, the Ok&Jetzt series at the 12-14contemporary Gallery, and at Medienwerkstatt Wien?
Having exhibited in COVID times, I found it interesting what solutions would pop up to still show the works. An interesting situation took place when exhibiting the Roomtour AR for the first time, where I would walk through virtual room in the gallery with my phone in my hand, running the AR-App. The screen from my phone was streamed to another TV-screen pointing towards the street, so the people outside could see what was happening on the phone. To get to see the digital objects you had to look through 3 times glass, i still love that thought. Additionally, the whole thing was streamed for the people at home sitting in their rooms again. All this inversions/loops made it an unusual, but also great time for me. Special thanks to the people of the 12-14contemporary gallery, which is now called discotec, I urge you to check the place out, when in Vienna.
– How has the Digital Art program led by Ruth Schnell at the University of Applied Arts Vienna influenced your work?
Yes, definitely. Seeing and hearing so many different approaches to art at this great class has made me grow a lot. I learned so many different expert techniques, from soldering to game engine stuff. If you happen to be in Vienna and they have an exhibition on, go see it. Shout out and big hugs to everyone there!
– Could you delve into the creative process behind “Roomtour AR”? How did you use 3D camera tracking techniques to extract data from a YouTube video?
When I discovered there was an influencer trend online (mostly on YouTube at that time) where people just show off their homes i was kind of baffled. First off I couldn’t imagine how this could be of so much interest to become a trend, because everyone was basically showing the same IKEA furniture. Thinking of how many wasted Gigabytes of data this was, i became interested on how much data could be extracted from such a video.
If you have movement in your camera, know the focal length of the camera and have enough visual cues, software can generate 3D geometry from 2D images. It is basically the same as photogrammetry, only slightly different. Using this technique I was able to reconstruct parts of an influencers room in real scale from a single video. It’s not very precise and glitches a lot, but I like also the parts where the software tries to understand and compensates some parts artificially.

Additionally, I let image and speech recognition run over the video and placed the data in the room. Together it forms an AR Experience, where you can walk through a room of accumulated, extracted data, see the original camera movements and read the original spoken text. Of course I am not sharing the source of the video.
– Are there risks associated with the data we publish online?
Or if you ask Chat-GPT which likes to build on this distorted reality:
Yes, there are several risks associated with the data we publish online. Here are some of the main risks to consider:
- Privacy and Personal Information Exposure: Publishing personal information online, such as your full name, address, phone number, and even details about your daily activities, can make you susceptible to identity theft, stalking, and harassment.
- Data Breaches: When you share information on websites, social media platforms, or other online services, there’s a risk that the data could be compromised in a data breach. This could lead to your personal information, passwords, and other sensitive data being exposed and potentially misused.
- Cyberbullying and Harassment: Sharing information online can make you a target for cyberbullying and harassment. Once information is out there, it can be difficult to control who has access to it and how they use it.
- Reputation Damage: Content you publish online can have a lasting impact on your reputation. Inappropriate or offensive posts, photos, or comments can affect how you’re perceived by friends, family, colleagues, and potential employers.
- Data Mining and Profiling: Companies often collect and analyze data about your online behavior to create profiles for targeted advertising. This can lead to a loss of privacy and bombardment with ads tailored to your interests, which some people find invasive.
- Phishing and Scams: Sharing personal information online makes you more vulnerable to phishing attacks and scams. Cybercriminals can use the information you’ve shared to craft convincing messages that trick you into revealing more sensitive data or money.
- Geolocation and Location Tracking: Many online platforms collect location data, which can be used to track your movements and habits. This information could potentially be misused by individuals with malicious intent.
- Employment and Legal Consequences: Content you post online, even on private accounts, can sometimes be accessed by potential employers, leading to employment-related consequences. Additionally, sharing illegal or controversial content can lead to legal issues.
- Permanent Record: Once something is published online, it’s often difficult to completely remove it. Even if you delete a post or a photo, it might have already been saved, shared, or archived by others.
- Loss of Control: When you share data online, you lose a degree of control over how it’s used and who has access to it. It’s possible for your data to end up in places you didn’t intend, and it can be challenging to reclaim that control.
To mitigate these risks, it’s important to practice good online hygiene:
- Be cautious about sharing personal information.
- Regularly review and adjust your privacy settings on social media platforms.
- Use strong, unique passwords for different online accounts.
- Think before you post, considering the potential consequences.
- Educate yourself about common online scams and phishing tactics.
- Be aware of the data usage policies of the websites and platforms you use.
Remember that while the internet offers many benefits, it’s essential to be mindful of the potential risks and take steps to protect your online presence and personal information.
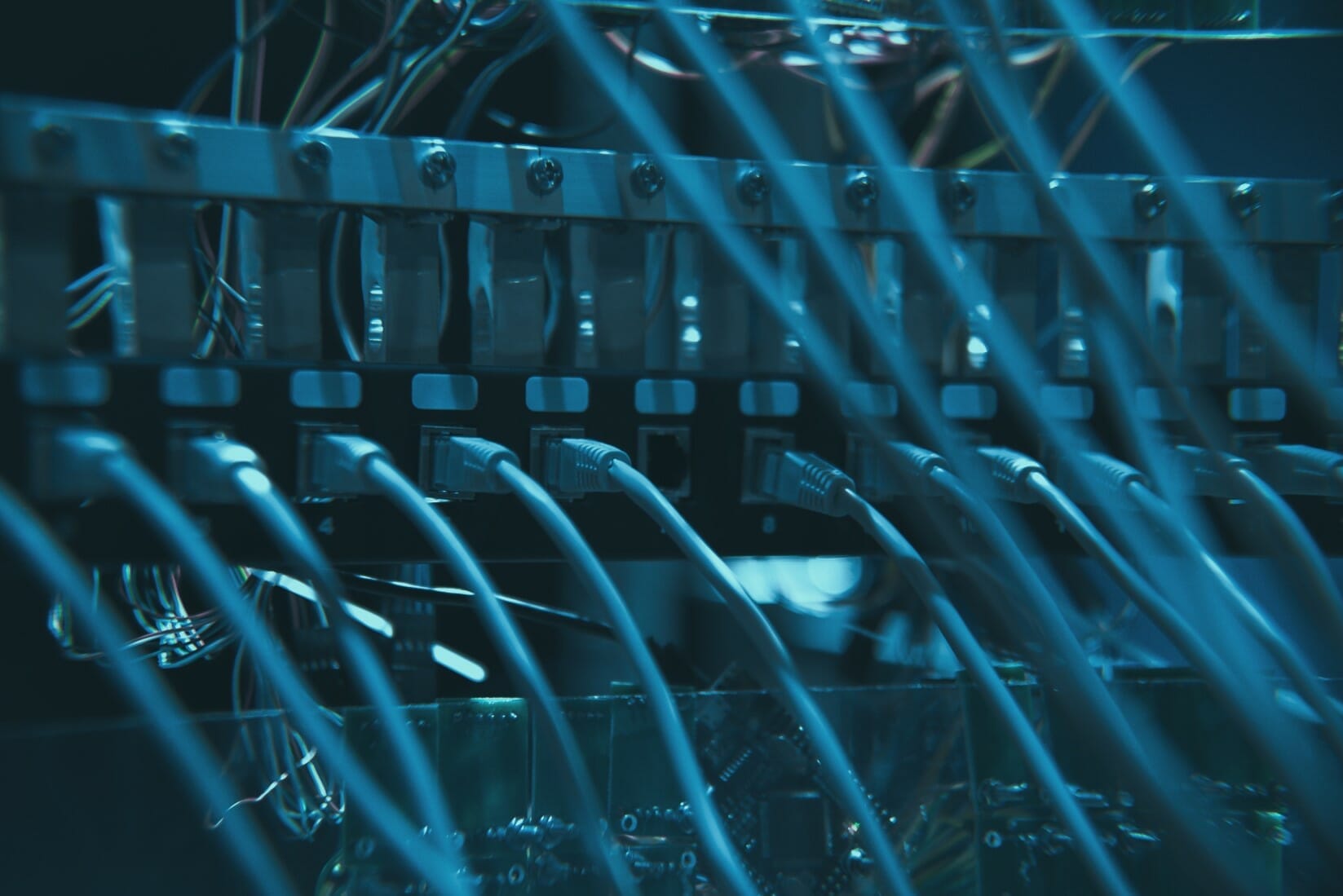
– Could you describe the performance “Decoding it the hard way”? What do the two servers linked by 96 network cables symbolize?
The performance together with Lea Karnutsch is about half an hour long and describes a certain kind persona in a network, in this case a hacker persona or someone who is trying to exploit the boundaries of a system. The two server racks symbolize a network with the connections laid open. Searching for a string of value and/or sense the performer is attacking the system with brute force, shown by Lea pulling and strangling the cables.
When pulling on the cables, a sensor is activated, which alters the sound of the music being played live by myself. While Lea embodies the hacker persona and dances in the cable, my role shows a person that keeps the network alive just by living in it.
– What artistic references do you have within the history of art (including strictly contemporary/current history)?
I take a lot of inspiration from earlier (classical?) media art and it’s theories. To name anyone specific is hard, but I do love James Bridle’s works (thats a lot more recent though).

– In your work “Sibling Inference”, what does the behavior of the commercially available camera drone mean in relation to the military drone?
In “Sibling Inference” a camera drone is following the projected moving images of war drones. I’ve trained a Machine Learning Network on about 800 images of war drones and programmed the autonomous controls of the drone.
The drone cannot reflect as it has no mind of its own, but the installation makes it look like it does. Seeing and following its martial sister’s movements and actions, it has to position itself. Basically, it uses the technical principles that are use for finding people in war zones, object detection and classification. This drone only follows drones, though you can program it to follow anything visible – but happens if the classification is wrong? Who will be responsible if something bad happens and to what extent should these machines decide on their own?



– You have worked on questioning autonomous warfare techniques and their impact on civilian technology, could you talk about it?
A lot of the things that surround us, are military inventions, or have been used in their early stages for military interests. While this is not a particularly new thing, I still find it very interesting how much of that persists in our everyday life. Are some of the root-assets of these technologies maybe hostile to basically everyone, or might this just be some natural progression?
– What is your point of view on the ethical implications of using artificial intelligence and machine learning in creating your works?
I think it’s important to know what the AI or machine learning system was built upon, at the moment you’re using it. We’ve all heard the horror storys of digital sweatshops in Africa, where workers had to flag „inappropiate“ content facing serious psychological stress after their long shifts. At the moment it feels like we’re been tested on a medicine that could have serious side effects, just for the sake of progress or financial profits of a few. But of course, you cannot just look away while some data scraping tool is looking basically everywhere.
Night Time Story
NIGHTTIMESTORY is a decentralized and online project that aims to be a platform for show a wide range of contemporary art forms, including visual art, videoart, conceptual art theory, NFTs, and critique.
You may also like
“Total Theatre ESP”at Belmacz, London
“Total Theatre ESP” by Bora Baboçi, Toby Christian, Michael Kleine, Cosima zu Knyphause
Fakewhale Solo Series presents Cathédrales Modernes by Chepertom
On Wednesday, May 15th, Fakewhale proudly presents “Cathédrales Modernes”, a Fakewhale Solo Ser
Julie Insun Youn, “Instant Trance” at Platform-L Contemporary Art Center, Seoul, South Korea.
“Instant Trance” by Julie Insun Youn at Platform-L Contemporary Art Center, Seoul, South






